Following my last post about how to hunt for malicious PowerShell commands, I'm interested to detect Mimikatz once it is launched through PowerShell, like for example with PowerShellEmpire framework. Mark Russinovich has just written that in order to detect Mimikatz you must monitor lsass.exe for process access.
So basically, I have created a simple filter in sysmon for event code 10 (ProcessAccess) with SourceImage PowerShell.exe and TargetImage lsass.exe
Image may be NSFW.
Clik here to view.

<ProcessAccessonmatch="include">
<SourceImagecondition="contains">powershell.exe</SourceImage>
<TargetImagecondition="contains">lsass.exe</TargetImage>
</ProcessAccess>
Now it is time to test if it works.
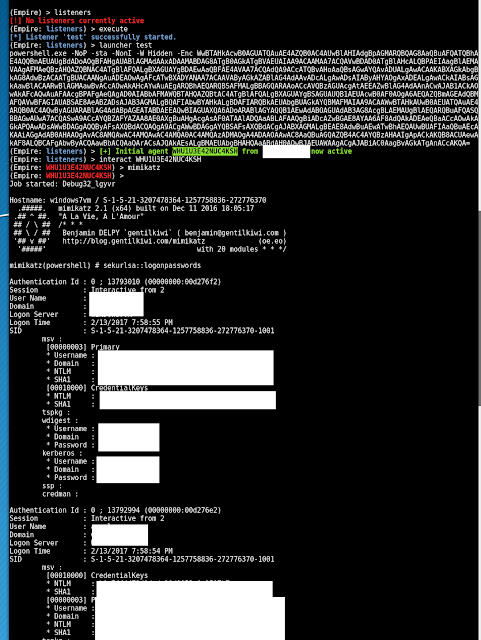
So I use the Mimikatz module in PowerShellEmpire
In Splunk I detect the initial encoded PowerShell Command
Image may be NSFW.
Clik here to view.

After a few second I run a SPL query to see when the PowerShell.exe command accesses the process lsass.exe, which it is when mimikatz is executed :)
Image may be NSFW.
Clik here to view.