Locky is a Ransomware which become active a few months ago. The threat actors behind this malware seems to be the same than Dridex (1 and 2)
The 12th of May there was a huge campaign of Locky hitting several countries, Switzerland was one of them.
The modus operandi is always the same than with Dridex: thousands of emails sent with a MS Word file attached which acts as dropper. The Word file contains some obfuscated VBA which download the malicious PE file. The word file was named "Document 2.docm" and had around 50k of size
In this case, the interesting part is that the MS Word Document looks empty when opening. This is a trick done by the cyber criminal to fool the victim, to make them thinking that the Macros needs to be enabled in order to see the content.
![]()
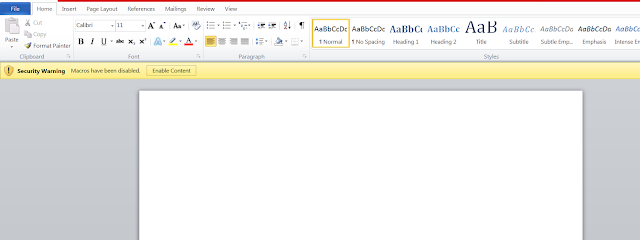
Then, once the macros is enable and the code script inside is executed, a PE file is downloaded. There are several URL from there the file is downloaded, however the file has the same name "nbtv64cvh".
URLs example: www.soft-med.za.pl/nbtv64cvh & hate-metal.com/nbtv64cvh & startours.biz/nbtv64cvh
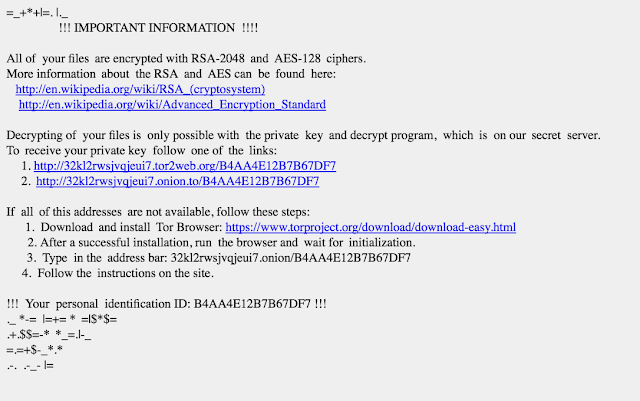
One the the PE is executed some files are encrypted:
![]()
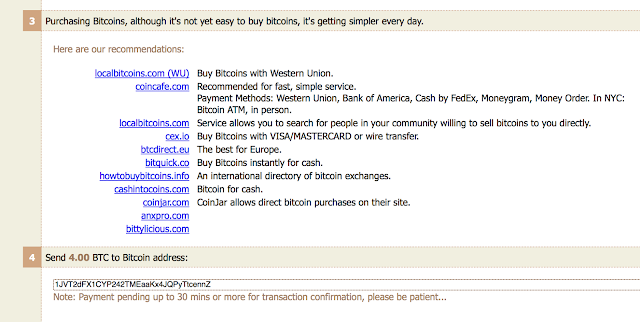
The bad guys ask for 4BTC to decrypt the files:
![]()
Yesterday, during a few hours, again, there was another big campaign using exactly the same technique: a blank Office document attached with some VBA, but in this case the name of the file was different each time"ORDER-XXX-YYYYYY-ZZZZ.docm", and the size was also different (around 70KB).
The dropped file in this case has the name "987t5t7g". Some IOC of domains where the PE resides: d2014890.instant.xoom.it, ramsayconstruction.ca, pdpenews.com, navasdetolosa.com, visionaero.com, researchusainc.com
Some samples:
f724e435d31f4ce95631f79535f449b9
80fea3fdad89785527d9a520aaeef463
b9ff7190438e4e85ce4aa34097b58825
66f5c6cb07accb9b252b117906614bf1
8aa254efcabd320e26b5d38ee7f92b94
6920f1c61a22c85410628f118b54ec53
3aaff9294cabb5ea33108b883c273eba
f7c755da161f5b30c2a6c5e3c747fd7c
235d1aad0419cb86e2e76e96c44e7f16
4abc37a25aa5a4d002392a33d4cea185
Today, there is still ongoing another campaign using exactly the same kind of MS office blank document. In this case the name of the document is different each time "Bill_xxxx.docm" and the size is around 52KB. The dropped file is "89yg67no"
Some indicators:
001e17ddb4b5257813687c7f7802cf96
dc108f9d544d0078e4756a30f3e104ee
05d5d301709fbf316e859b34c042cbf5
3ede700188cef3be51519c7cc29ff17e
c265420431e3e0e30ffd78596d508b30
dd229e755f21c690978ac3e0b51caa11
a6d652f8991f373dc5b7a058b94e1787
c98f28f69bda4cc0cb2ea24555839a1f
the-merchant-account-advisor.com
www.robtozier.com
visionaero.com
protei.me
Happy hunting!
URLs example: www.soft-med.za.pl/nbtv64cvh & hate-metal.com/nbtv64cvh & startours.biz/nbtv64cvh
One the the PE is executed some files are encrypted:
The bad guys ask for 4BTC to decrypt the files:
Yesterday, during a few hours, again, there was another big campaign using exactly the same technique: a blank Office document attached with some VBA, but in this case the name of the file was different each time"ORDER-XXX-YYYYYY-ZZZZ.docm", and the size was also different (around 70KB).
The dropped file in this case has the name "987t5t7g". Some IOC of domains where the PE resides: d2014890.instant.xoom.it, ramsayconstruction.ca, pdpenews.com, navasdetolosa.com, visionaero.com, researchusainc.com
Some samples:
f724e435d31f4ce95631f79535f449b9
80fea3fdad89785527d9a520aaeef463
b9ff7190438e4e85ce4aa34097b58825
66f5c6cb07accb9b252b117906614bf1
8aa254efcabd320e26b5d38ee7f92b94
6920f1c61a22c85410628f118b54ec53
3aaff9294cabb5ea33108b883c273eba
f7c755da161f5b30c2a6c5e3c747fd7c
235d1aad0419cb86e2e76e96c44e7f16
4abc37a25aa5a4d002392a33d4cea185
Today, there is still ongoing another campaign using exactly the same kind of MS office blank document. In this case the name of the document is different each time "Bill_xxxx.docm" and the size is around 52KB. The dropped file is "89yg67no"
Some indicators:
001e17ddb4b5257813687c7f7802cf96
dc108f9d544d0078e4756a30f3e104ee
05d5d301709fbf316e859b34c042cbf5
3ede700188cef3be51519c7cc29ff17e
c265420431e3e0e30ffd78596d508b30
dd229e755f21c690978ac3e0b51caa11
a6d652f8991f373dc5b7a058b94e1787
c98f28f69bda4cc0cb2ea24555839a1f
the-merchant-account-advisor.com
www.robtozier.com
visionaero.com
protei.me
Happy hunting!